The Comprehensive Guide to Security Risk Assessments, Second Edition: Protecting Your Organization from Cyber Threats

4.3 out of 5
| Language | : | English |
| File size | : | 6657 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 495 pages |
In the ever-changing digital landscape, where cyber threats are constantly evolving, the security of your organization is paramount. Security risk assessments are an essential component of a comprehensive cybersecurity strategy, providing a systematic approach to identifying, evaluating, and mitigating potential vulnerabilities.
This second edition of the Comprehensive Guide to Security Risk Assessments provides an authoritative and up-to-date resource for security professionals, risk managers, and IT leaders. Drawing on industry best practices and real-world case studies, this comprehensive guide offers a step-by-step methodology for performing effective security risk assessments.
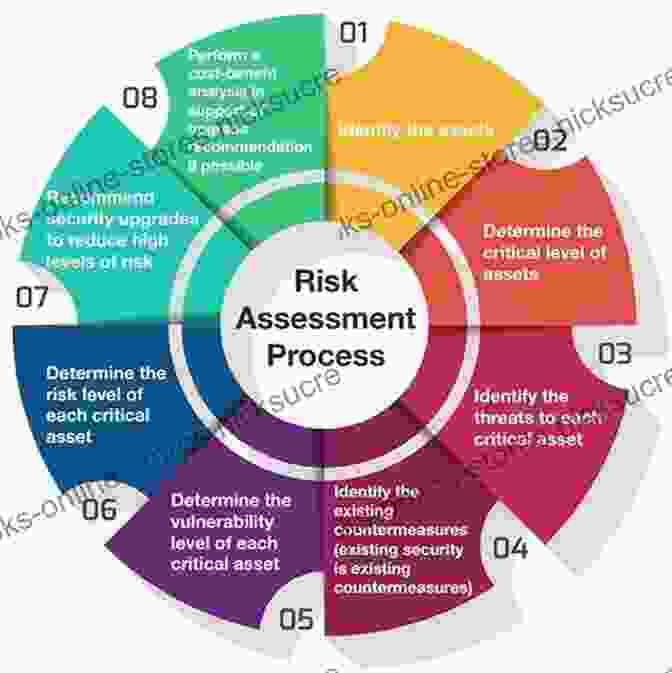
Step-by-Step Security Risk Assessment Methodology
The guide outlines a structured and comprehensive methodology that encompasses the following key steps:
- Planning and Preparation: Define the scope, objectives, and stakeholders involved in the assessment.
- Asset Identification and Valuation: Identify critical assets and their value to the organization.
- Threat and Vulnerability Identification: Analyze potential threats and vulnerabilities that could compromise assets.
- Risk Assessment and Analysis: Evaluate the likelihood and impact of identified risks.
- Risk Mitigation and Control Selection: Develop and implement control measures to mitigate identified risks.
- Assessment Reporting and Communication: Document and communicate assessment findings to stakeholders.
- Assessment Monitoring and Review: Continuously monitor and review the assessment to ensure its effectiveness.
Key Features of the Second Edition
The second edition of the Comprehensive Guide to Security Risk Assessments offers a range of enhancements, including:
- Updated content: Reflects the latest industry standards, regulations, and best practices.
- Expanded coverage: Includes new sections on risk quantification, cloud computing security, and mobile device security.
- Real-world case studies: Provides practical examples of how organizations have successfully implemented security risk assessments.
- Interactive tools and resources: Offers online templates, calculators, and checklists to assist with the assessment process.
Benefits of Conducting Security Risk Assessments
Regularly conducting security risk assessments provides numerous benefits for organizations, including:
- Enhanced cybersecurity posture: Identify and address vulnerabilities before they are exploited.
- Compliance with regulatory requirements: Meet industry standards and regulations that require security risk assessments.
- Improved resource allocation: Prioritize cybersecurity investments based on risk.
- Reduced insurance premiums: Demonstrate a commitment to cybersecurity and qualify for premium reductions.
- Increased customer and stakeholder confidence: Assure stakeholders that their data and systems are protected.
The Comprehensive Guide to Security Risk Assessments, Second Edition is an indispensable resource for any organization looking to strengthen its cybersecurity posture. By following the step-by-step methodology outlined in this guide, organizations can effectively identify, assess, and mitigate security risks, ensuring their continued resilience in the face of evolving cyber threats.
Invest in this guide today and take a proactive approach to protecting your organization from the ever-changing cybersecurity landscape.
4.3 out of 5
| Language | : | English |
| File size | : | 6657 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 495 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Best Book Source
Best Book Source Ebook Universe
Ebook Universe Read Ebook Now
Read Ebook Now Digital Book Hub
Digital Book Hub Ebooks Online Stores
Ebooks Online Stores Fiction
Fiction Non Fiction
Non Fiction Romance
Romance Mystery
Mystery Thriller
Thriller SciFi
SciFi Fantasy
Fantasy Horror
Horror Biography
Biography Selfhelp
Selfhelp Business
Business History
History Classics
Classics Poetry
Poetry Childrens
Childrens Young Adult
Young Adult Educational
Educational Cooking
Cooking Travel
Travel Lifestyle
Lifestyle Spirituality
Spirituality Health
Health Fitness
Fitness Technology
Technology Science
Science Arts
Arts Crafts
Crafts DIY
DIY Gardening
Gardening Petcare
Petcare Gabriel Davis
Gabriel Davis Adam Winkler
Adam Winkler Matt Picheny
Matt Picheny Daniel Allen
Daniel Allen Phyllida Law
Phyllida Law Graham Norton
Graham Norton Klaus Leopold
Klaus Leopold Adrian Wojnarowski
Adrian Wojnarowski Patti Lupone
Patti Lupone Manuel Becvar
Manuel Becvar 3rd Edition Kindle Edition
3rd Edition Kindle Edition Marci Ien
Marci Ien Bill Ranauro
Bill Ranauro Patty Kirk
Patty Kirk Amir Khan
Amir Khan Warith Niallah
Warith Niallah Elizabeth Warnock Fernea
Elizabeth Warnock Fernea Nigel Slater
Nigel Slater Robin Gerber
Robin Gerber John Elkington
John Elkington
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 George MartinIn Search Of Serenity: A Journey Through Tranquil Landscapes And Spiritual...
George MartinIn Search Of Serenity: A Journey Through Tranquil Landscapes And Spiritual...
 Clarence MitchellBritish Coastal Wildlife Collins Complete Guides: Uncovering the Wonders of...
Clarence MitchellBritish Coastal Wildlife Collins Complete Guides: Uncovering the Wonders of... Javier BellFollow ·19.1k
Javier BellFollow ·19.1k Brayden ReedFollow ·19.9k
Brayden ReedFollow ·19.9k Elmer PowellFollow ·15.7k
Elmer PowellFollow ·15.7k Nathaniel PowellFollow ·18k
Nathaniel PowellFollow ·18k Henry David ThoreauFollow ·16.2k
Henry David ThoreauFollow ·16.2k Jack PowellFollow ·10.2k
Jack PowellFollow ·10.2k Sean TurnerFollow ·2.7k
Sean TurnerFollow ·2.7k Ivan TurgenevFollow ·11.5k
Ivan TurgenevFollow ·11.5k

 Hank Mitchell
Hank MitchellStories of War from the Women Reporters Who Covered...
The Vietnam War was one of the most...

 George Bell
George BellThe Hero and Saint of Islam: A Perennial Philosophy
Ali ibn Abi Talib,...

 Samuel Ward
Samuel WardWhispers and Shadows: A Naturalist's Memoir of Encounters...
In her lyrical...

 Clarence Brooks
Clarence BrooksRace, Gender, and Intellectual Property Rights in...
Dance is a powerful...

 Kirk Hayes
Kirk HayesThe Political Odyssey of Nick Galifianakis: From...
The American...

 Dean Butler
Dean ButlerGuibert of Nogent: A Portrait of the Medieval Mind
Guibert of Nogent was a...
4.3 out of 5
| Language | : | English |
| File size | : | 6657 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 495 pages |